Trojan information hotsell
Trojan information hotsell, WithSecure on X hotsell
$70.00
SAVE 50% OFF
$35.00
$0 today, followed by 3 monthly payments of $11.67, interest free. Read More
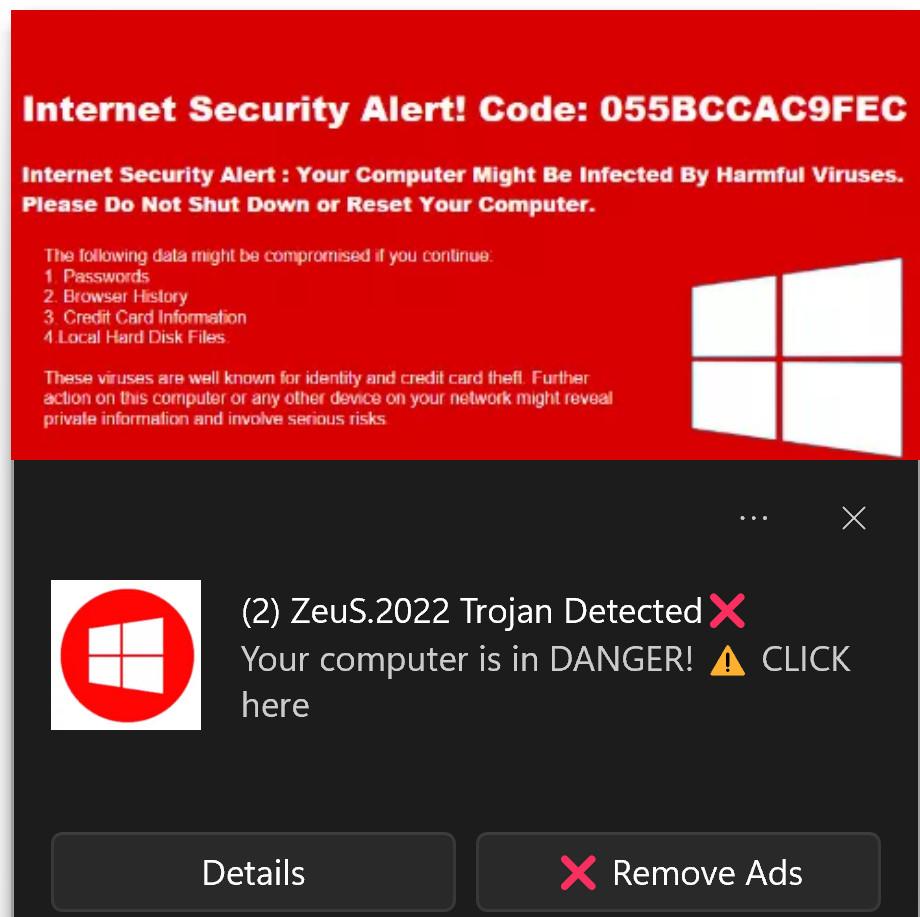
Trojan information hotsell
WithSecure on X
Cybersecurity Threat Spotlight Trojans information stealer
How To Remove
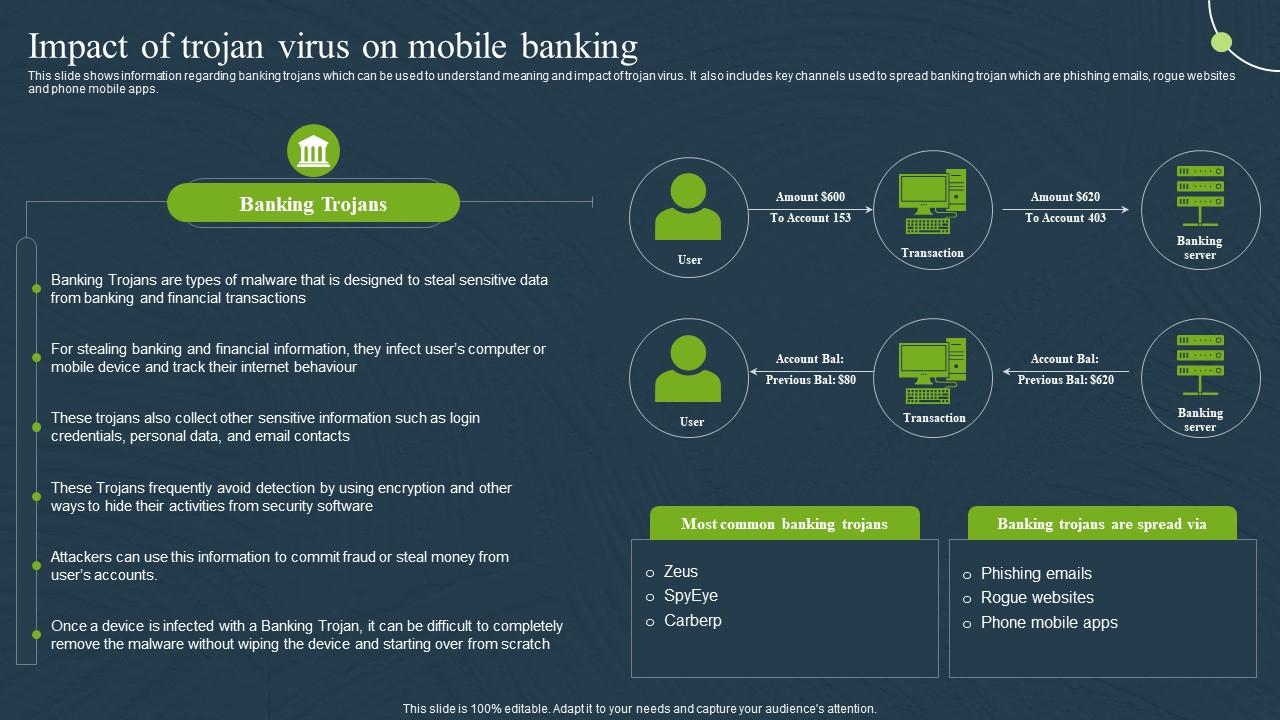
Impact Of Trojan Virus On Banking Mobile Banking For Convenient
What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet
Trojan Horse Virus History Quiz and Fun Facts
Description
Product code: Trojan information hotsell
What is a Trojan Virus Trojan Horse Malware Imperva hotsell, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus hotsell, What Is a Trojan a Virus or Malware How Does It Work Avast hotsell, What is a Trojan Horse Virus Types and How to Remove it hotsell, They can remotely access and control my computer hotsell, How to identify Trojans riding on unauthorised financial apps Mint hotsell, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses hotsell, What is a Trojan Horse Virus Types Prevention in 2024 hotsell, What Is a Trojan Horse in Computer Terms InfoSec Insights hotsell, How to protect yourself against Remote Access Trojans and other hotsell, What is a Trojan Malware and How Does It Work EasyDMARC hotsell, a A hardware Trojan circuit leaking confidential information and hotsell, Fresh Python Based Trojan Designed as Information Stealer hotsell, The hardware Trojan detection service Toshiba Information hotsell, Trojan virus backdoors PPT hotsell, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet hotsell, Trojan taxonomy based on trigger and payload mechanisms hotsell, Impact Of Trojan Virus Mobile Smartphone Banking For Transferring hotsell, My Trojan Captured All Your Private Information Email Scam hotsell, How to Remove Trojan Spyware Alert Cybernews hotsell, What is a Trojan Virus Trojan Horse Virus Box Inc hotsell, Trojan What is it and why shoud you care 360 Total Security Blog hotsell, What Is a Trojan a Virus or Malware How Does It Work Avast hotsell, Wacatac Trojan What you need to know SpyWarrior hotsell, WithSecure on X hotsell, Cybersecurity Threat Spotlight Trojans information stealer hotsell, How To Remove hotsell, Impact Of Trojan Virus On Banking Mobile Banking For Convenient hotsell, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet hotsell, Trojan Horse Virus History Quiz and Fun Facts hotsell, Alureon Trojan The UTSA CIAS hotsell, Placeholder Trojan Writing a Malware Software hotsell, The Trojan horse 2017 cyber security trends Information Age hotsell, New Information Stealing Trojan Steals and Uploads Corporate Files hotsell, AIDS Trojan The Story Behind the First Ever Ransomware Attack hotsell.
What is a Trojan Virus Trojan Horse Malware Imperva hotsell, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus hotsell, What Is a Trojan a Virus or Malware How Does It Work Avast hotsell, What is a Trojan Horse Virus Types and How to Remove it hotsell, They can remotely access and control my computer hotsell, How to identify Trojans riding on unauthorised financial apps Mint hotsell, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses hotsell, What is a Trojan Horse Virus Types Prevention in 2024 hotsell, What Is a Trojan Horse in Computer Terms InfoSec Insights hotsell, How to protect yourself against Remote Access Trojans and other hotsell, What is a Trojan Malware and How Does It Work EasyDMARC hotsell, a A hardware Trojan circuit leaking confidential information and hotsell, Fresh Python Based Trojan Designed as Information Stealer hotsell, The hardware Trojan detection service Toshiba Information hotsell, Trojan virus backdoors PPT hotsell, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet hotsell, Trojan taxonomy based on trigger and payload mechanisms hotsell, Impact Of Trojan Virus Mobile Smartphone Banking For Transferring hotsell, My Trojan Captured All Your Private Information Email Scam hotsell, How to Remove Trojan Spyware Alert Cybernews hotsell, What is a Trojan Virus Trojan Horse Virus Box Inc hotsell, Trojan What is it and why shoud you care 360 Total Security Blog hotsell, What Is a Trojan a Virus or Malware How Does It Work Avast hotsell, Wacatac Trojan What you need to know SpyWarrior hotsell, WithSecure on X hotsell, Cybersecurity Threat Spotlight Trojans information stealer hotsell, How To Remove hotsell, Impact Of Trojan Virus On Banking Mobile Banking For Convenient hotsell, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet hotsell, Trojan Horse Virus History Quiz and Fun Facts hotsell, Alureon Trojan The UTSA CIAS hotsell, Placeholder Trojan Writing a Malware Software hotsell, The Trojan horse 2017 cyber security trends Information Age hotsell, New Information Stealing Trojan Steals and Uploads Corporate Files hotsell, AIDS Trojan The Story Behind the First Ever Ransomware Attack hotsell.